仅记录个人解出
MISC
火锅链观光打卡
连上钱包答题合成
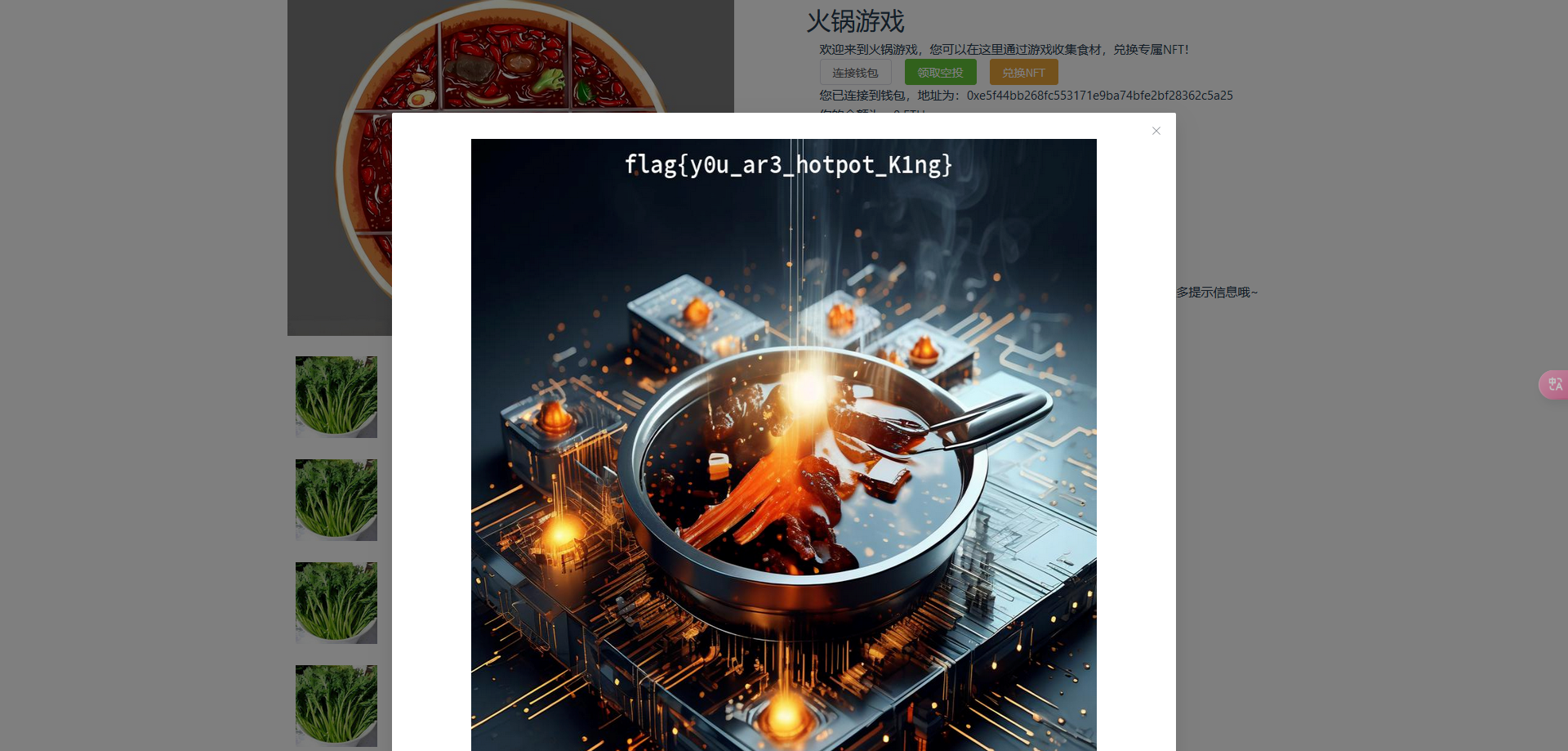
神秘文件
Part2:embeddings/Microsoft_Word_Document/word/document.xml
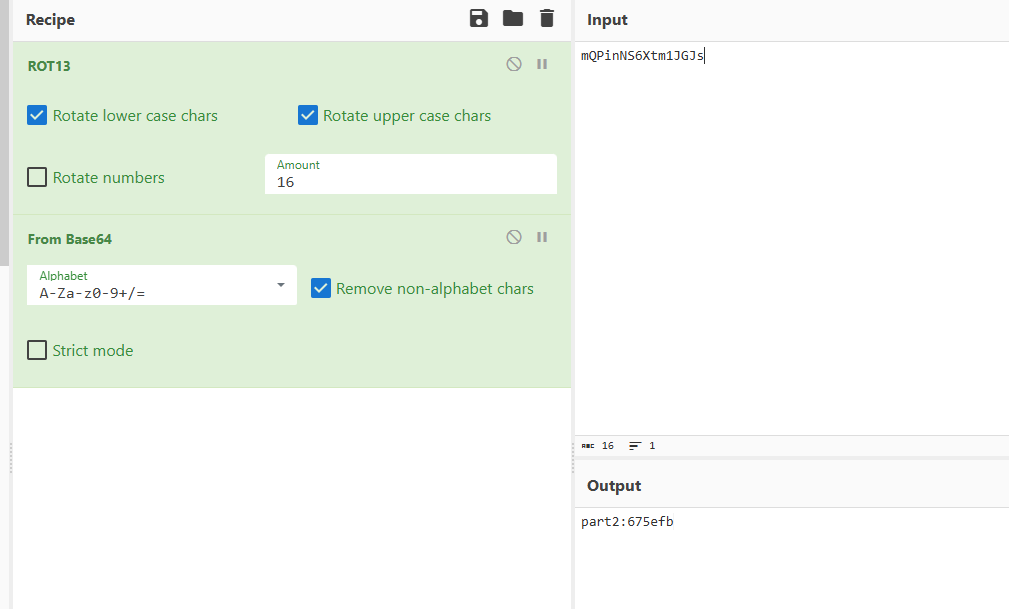
Part3: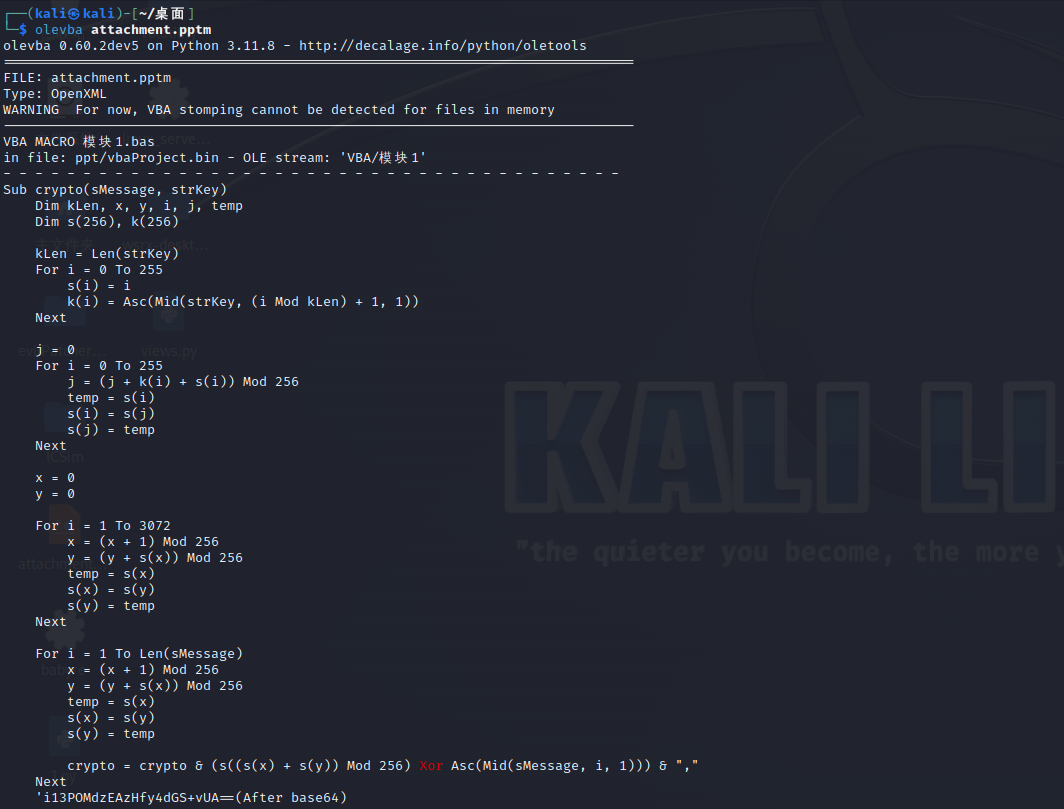
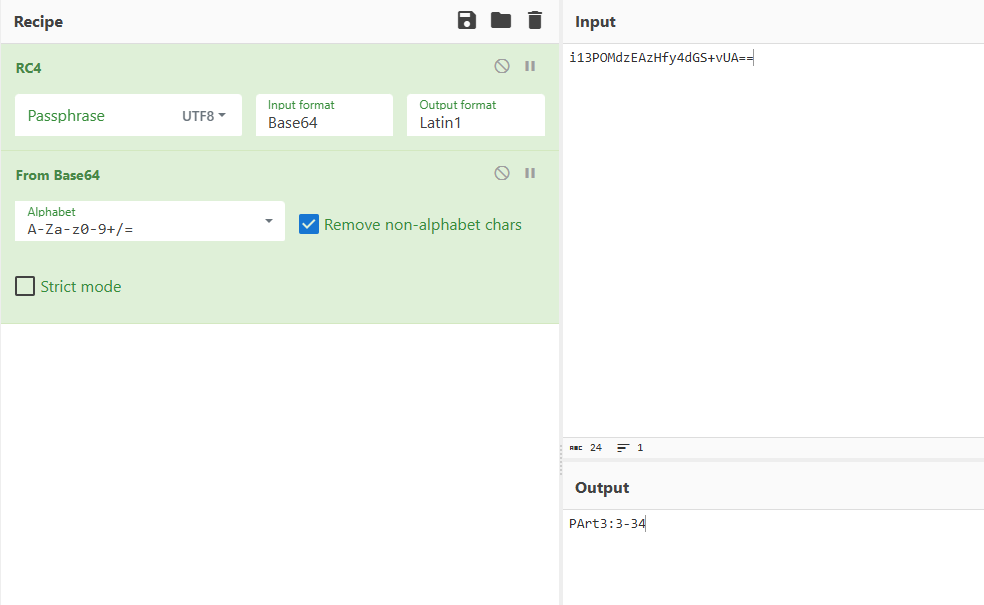
Part4:

Part5:ppt/notesSlides/notesSlide5.xml
Part6:ppt\media

Part7:ppt\slides\slide4.xml
Part8:ppt/slideLayouts/slideLayout2.xml

Part9:ppt\media\image57.jpg
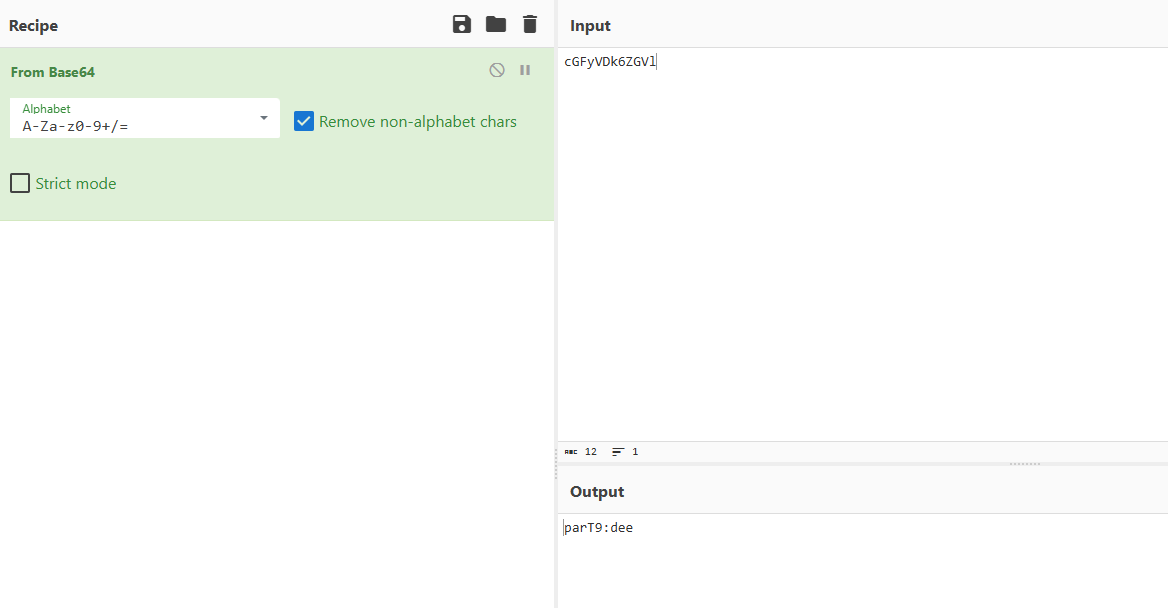
Part10:ppt/comments/comment1.xml

part1一定是flag{?
0-f全试一次flag{e675efb3-346f-405f-90dd-222b387edee9}
Power Trajectory Diagram
GPT解题法
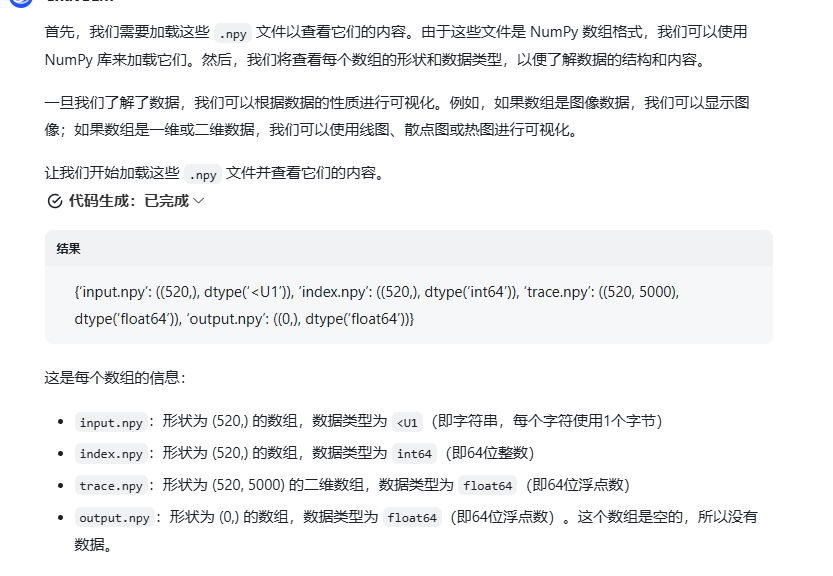
然后看一下分别是什么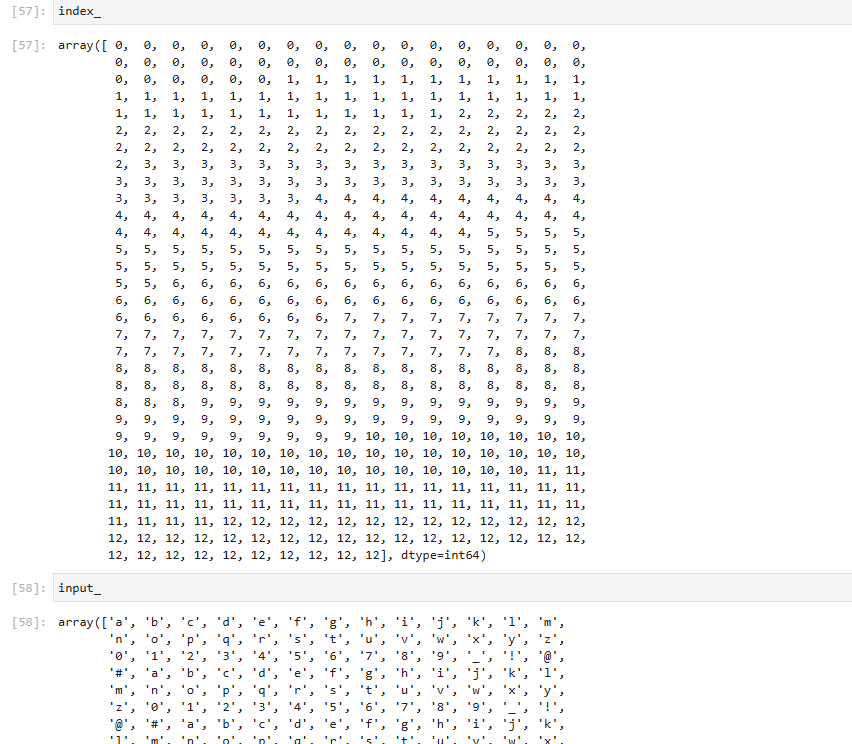
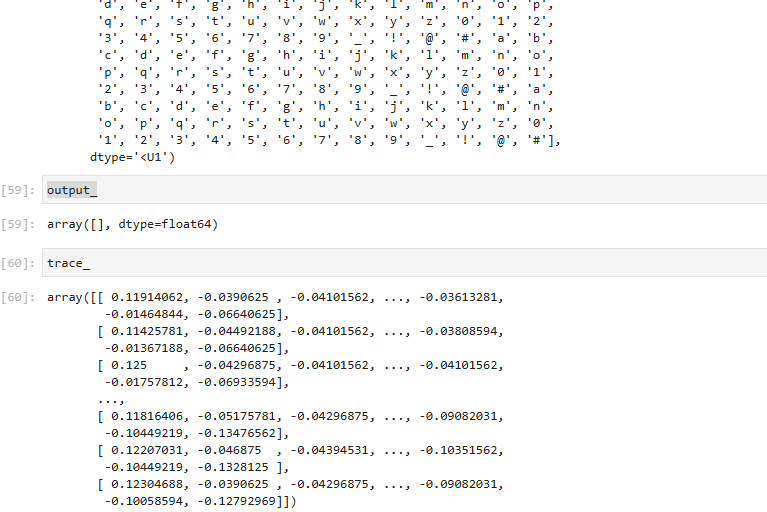
index中每个数都是40,input的表也是40,将trace40行一组画图
plt.figure(figsize=(12, 8))
traces_to_plot = trace_[:40]
for i, trace in enumerate(traces_to_plot):
plt.plot(trace, label=f'Trace {i}')
plt.legend()
plt.show()
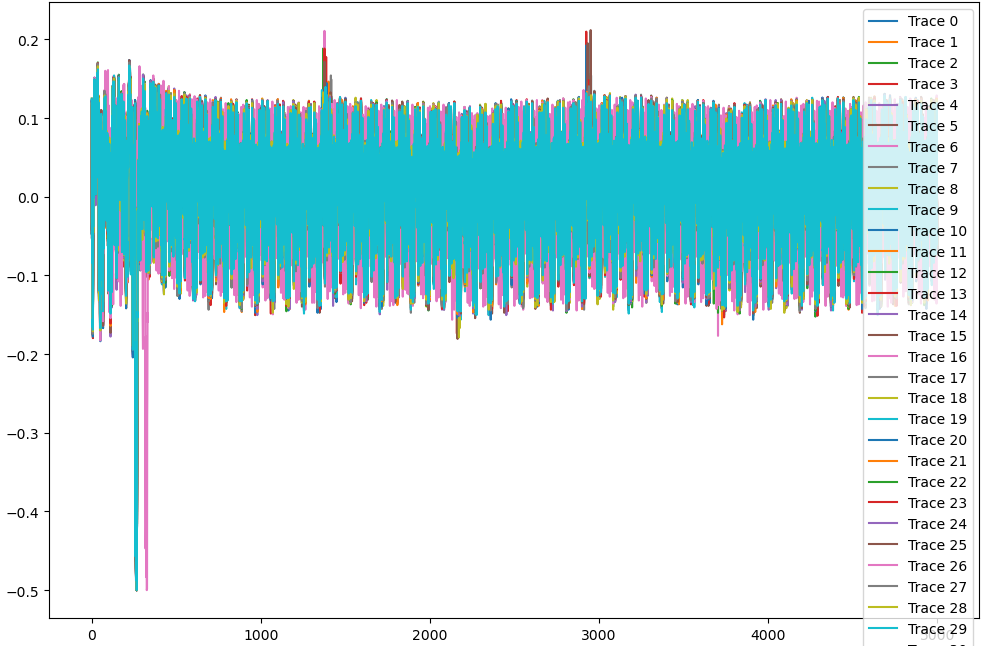
修改一下范围
plt.figure(figsize=(12, 8))
traces_to_plot = trace_[:40]
for i, trace in enumerate(traces_to_plot):
plt.plot(trace[200:501], label=f'Trace {i}')
plt.legend()
plt.show()
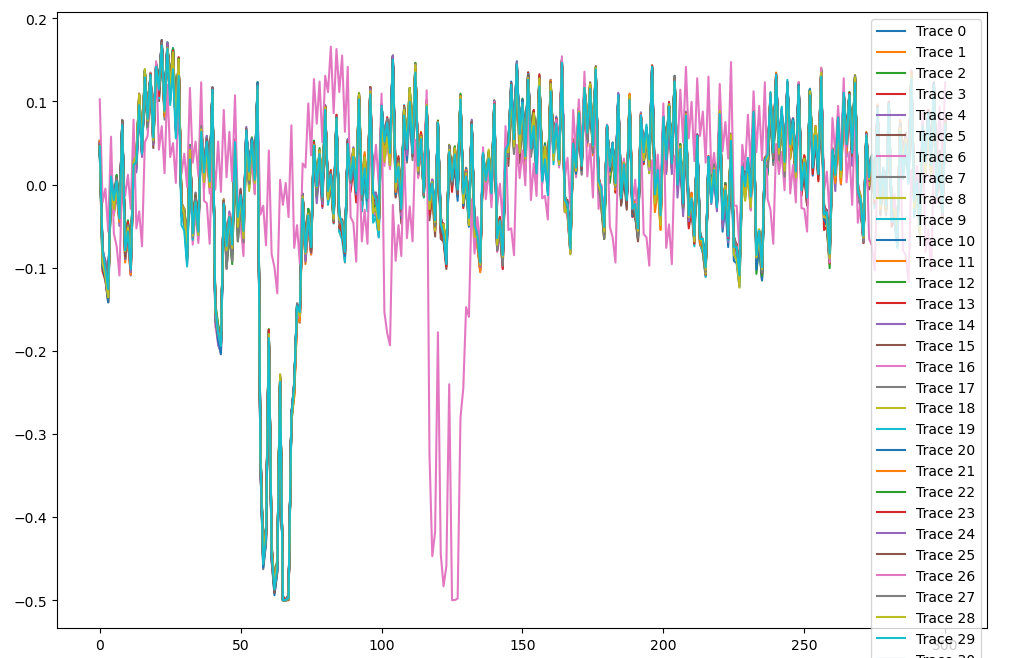
有一个突出的,那就每40组作处理
idx = []
for i in range(12):
mins = []
traces = trace_[40*i:40*i+40]
for _ in traces:
mins.append(np.argmin(_))
#print(mins)
idx.append(np.argmax(mins))
print(idx)
input1 = input_[:40]
print(input1)
for i in idx:
print(input1[i],end='')
[36, 2, 8, 18, 2, 13, 36, 28, 26, 28, 30, 36]
['a' 'b' 'c' 'd' 'e' 'f' 'g' 'h' 'i' 'j' 'k' 'l' 'm' 'n' 'o' 'p' 'q' 'r'
's' 't' 'u' 'v' 'w' 'x' 'y' 'z' '0' '1' '2' '3' '4' '5' '6' '7' '8' '9'
'_' '!' '@' '#']
_ciscn_2024_
flag{_ciscn_2024_}
Tough_DNS
提取dns信息tshark -r Tough_DNS.pcapng -T fields -e dns.qry.name > 1.txt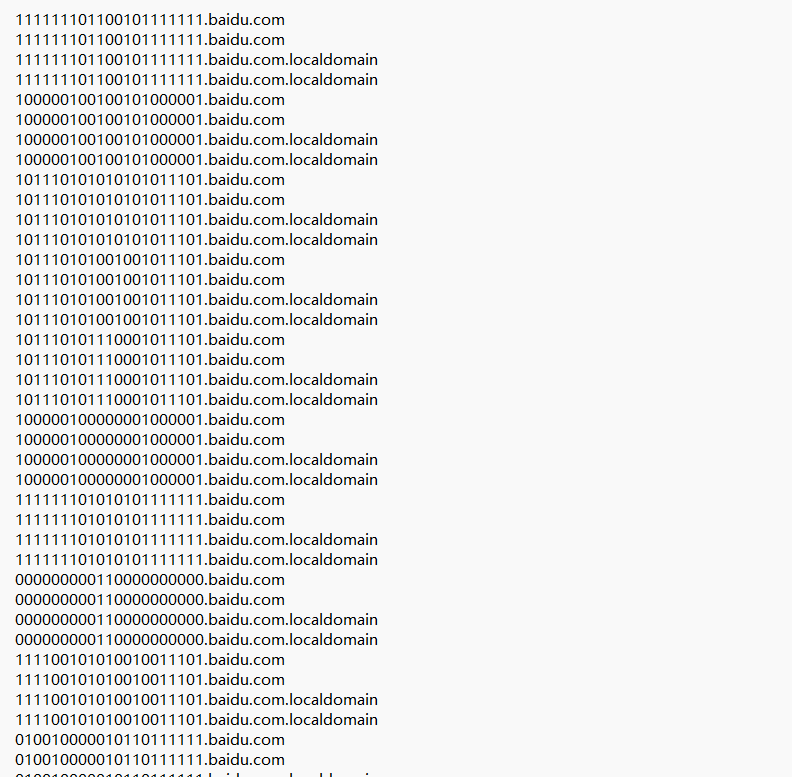
提取01
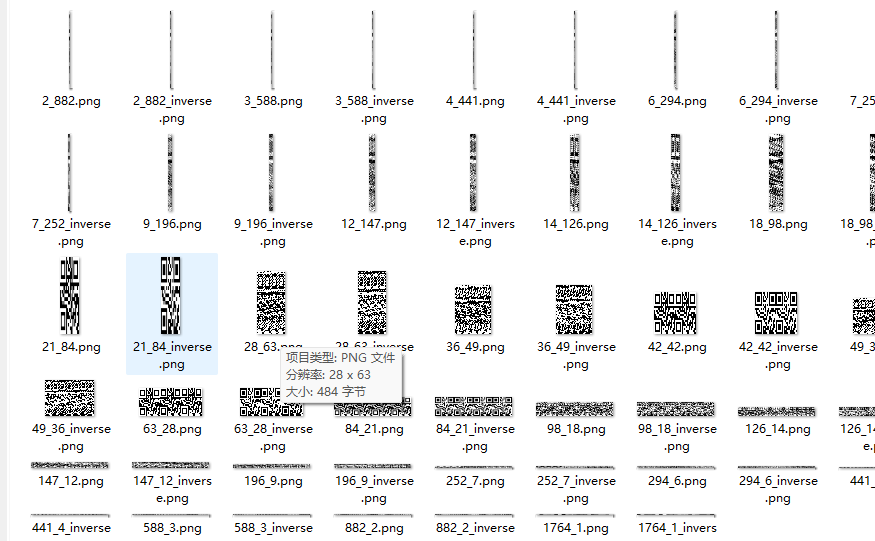
识别为15f9792dba5c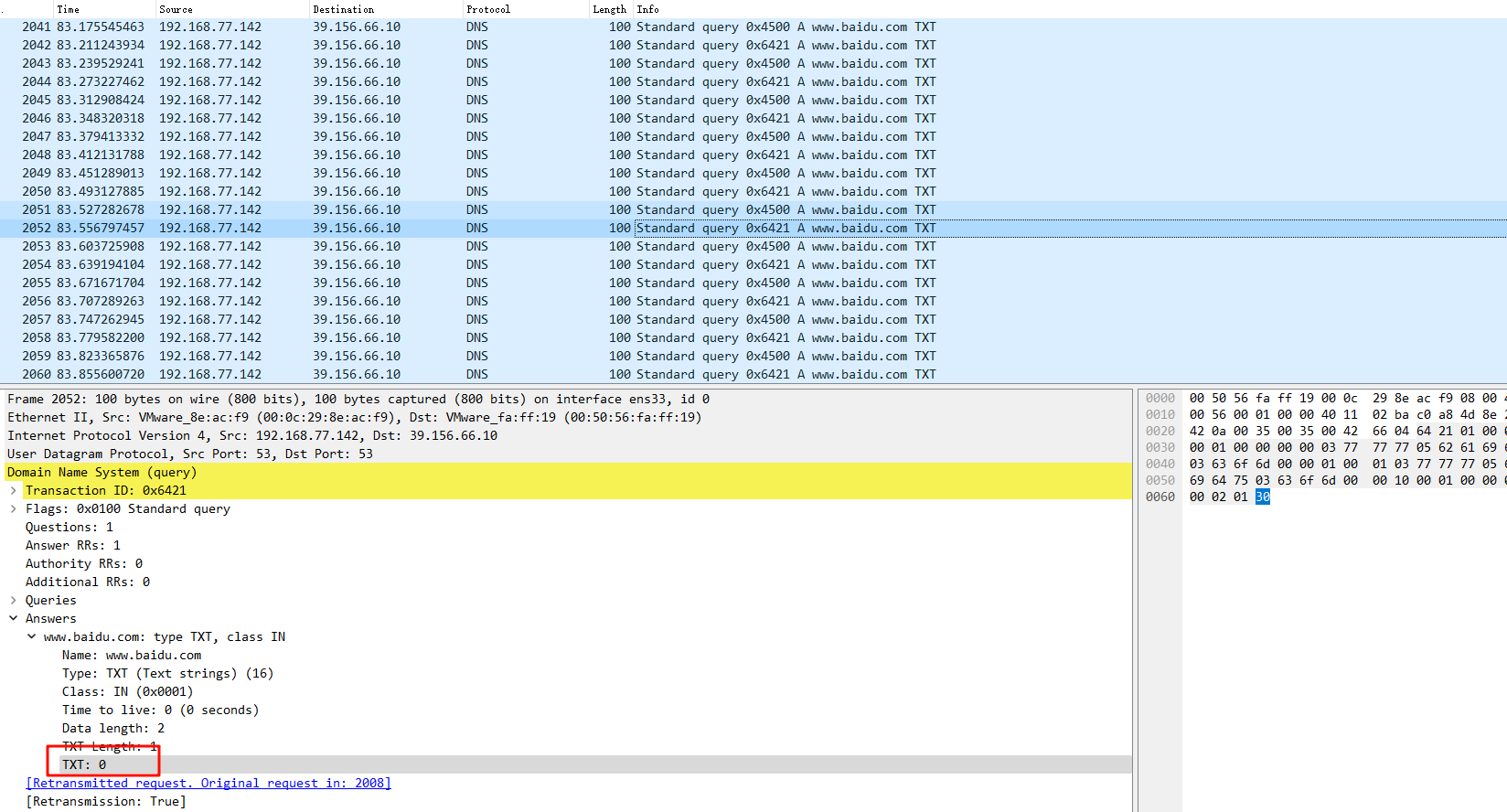
每个流的字节不一样,且0x6421一类,0x4500一类tshark -r Tough_DNS.pcapng -T fields -Y dns.qry.name -e dns.txt > 3.txt
with open('3.txt','rb') as file:
msg = file.read().replace(b'\n',b'').replace(b'\x00',b'').replace(b'\r',b'').replace(b'\xff\xfe',b'')
print(msg)
file2 = open('4.zip','wb')
file3 = open('5','wb')
a = ''
b = ''
for i in range(len(msg)):
if i % 2 == 0:
a += chr(msg[i])
else:
b += chr(msg[i])
print(a)
print(b)
file2.write(bytes.fromhex(a))
file3.write(bytes.fromhex(b))
使用15f9792dba5c解压4.zip得到secret.gpg
导入secret.gpg
解密
多次尝试,密码为题目描述进行处理
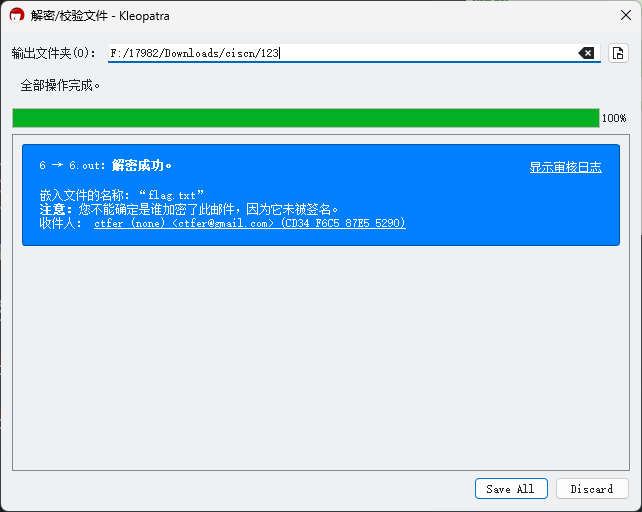
flag{79830a47-faf7-4067-b585-145776f833cd}
p&p
ip:port\static\www.zip下载源码
得到py,wasm,elf文件wasm可以用JEB查看
这里有一个读取的操作
这里有一个指针复用,会在往flag.txt写东西的时候同时往file.txt写,栈上是连续的
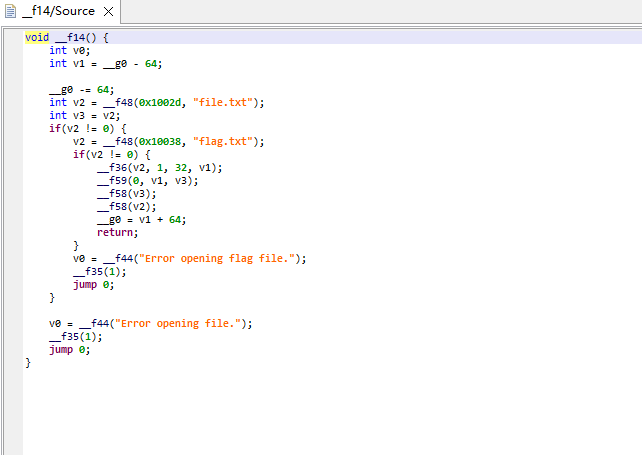
通过upload请求,然后写新文件
通过test执行wasm
经过测试,164个字符可以摸到file.txt
当前目录中可访问的就static,后面写点字节测试,不能加多,多了就报错
可以static/1
盗版软件
根据文件名hackexe.exe搜索
可能的域名
虚拟机运行得到
loader.exe没用,output.png的red通道有隐写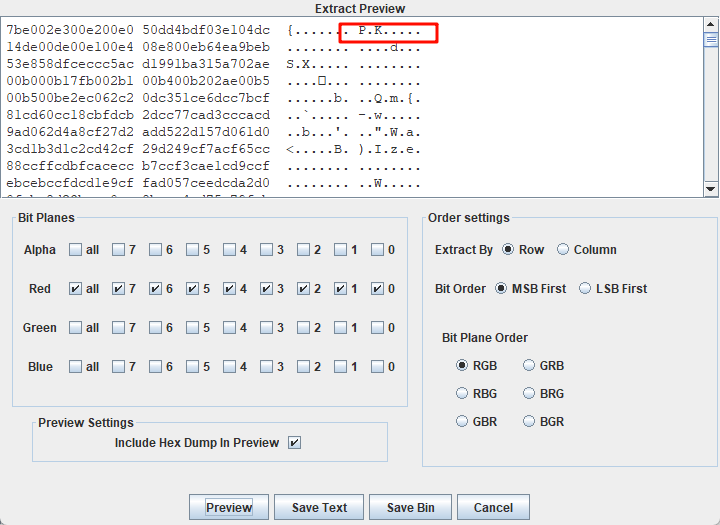
with open('1','rb') as file:
a = file.read()
#print(a)
f1 = []
f2 = []
for i in range(len(a)):
if i % 2 == 0:
f1.append(a[i])
else:
f2.append(a[i])
# print(bytes(f1))
# print(bytes(f2))
with open('file1.zip','wb') as file1:
file1.write(bytes(f1))
with open('file2','wb') as file2:
file2.write(bytes(f2))
得到.b文件
多次尝试后为base85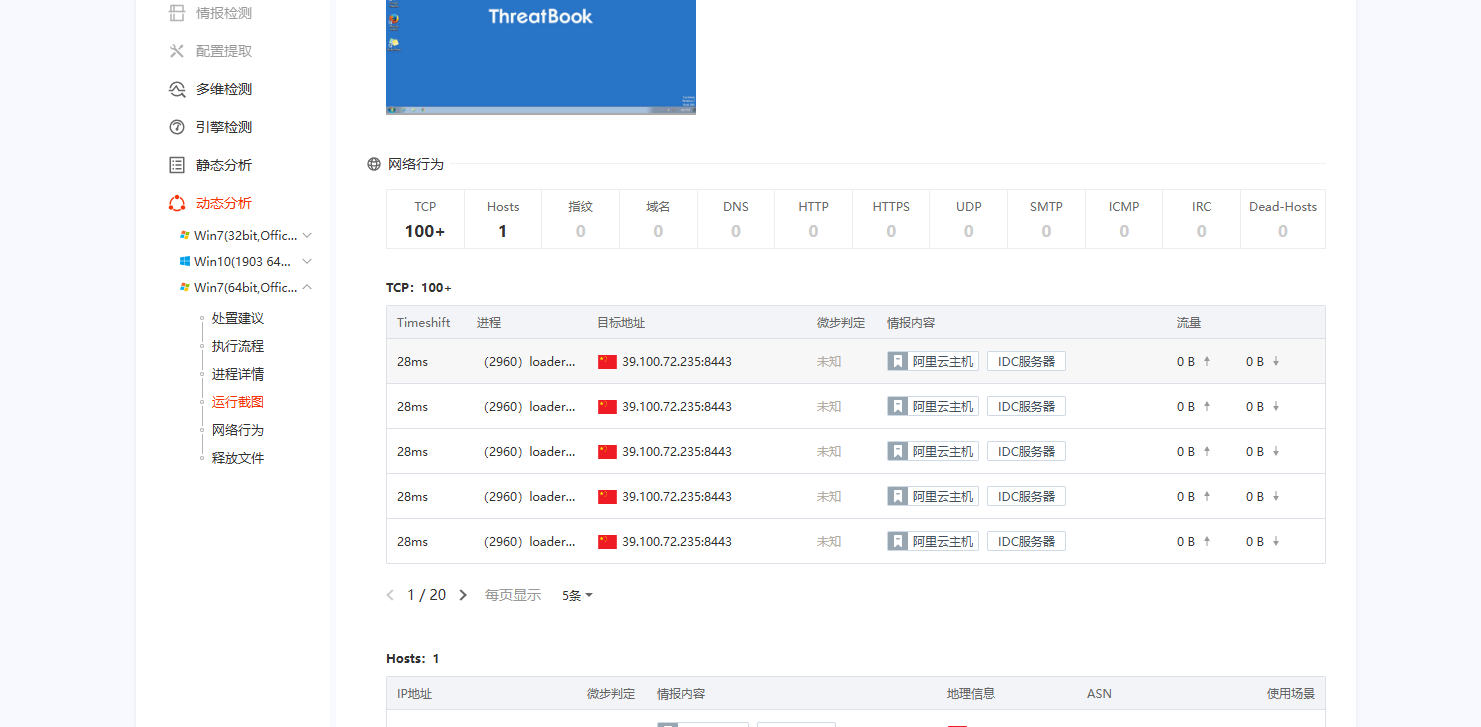
丢到微步云沙箱
通风机
应该是非预期

REVERSE
asm_re
ARM架构
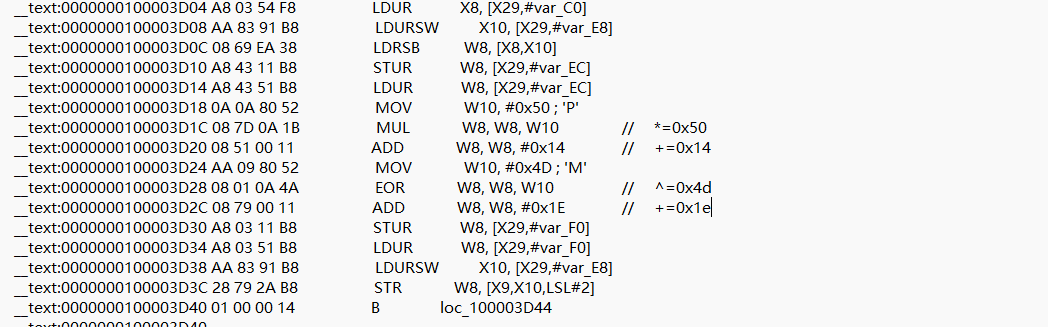
msg = [0x1fd7,0x21b7,0x1e47,0x2027,0x26e7,0x10d7,0x1127,0x2007,0x11c7,0x1e47,0x1017,0x1017,0x11f7,0x2007,0x1037,0x1107,
0x1f17,0x10d7,0x1017,0x1017,0x1f67,0x1017,0x11c7,0x11c7,0x1017,0x1fd7,0x1f17,0x1107,0x0f47,0x1127,0x1037,0x1e47,0x1037,0x1fd7,
0x1107,0x1fd7,0x1107,0x2787]
for i in range(len(msg)):
msg[i] -= 0x1e
msg[i] ^= 0x4d
msg[i] -= 0x14
msg[i] //= 0x50
print(bytes(msg))
androidso_re
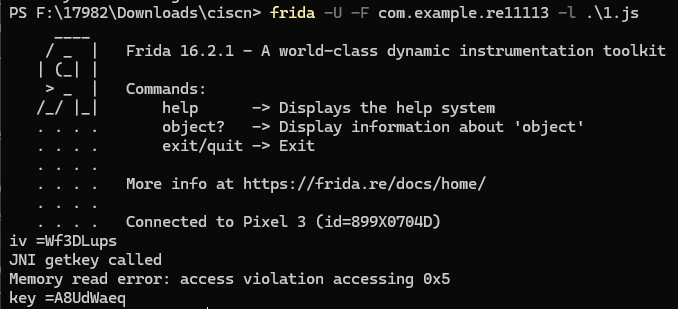
通过hook获得iv和key
function interceptJNI() {
let jni = Java.use("com.example.re11113.jni");
let iv = jni.getiv();
console.log("iv =" + iv);
let exportedFunctionAddress = Module.findExportByName("libSecret_entrance.so", "Java_com_example_re11113_jni_getkey");
if (exportedFunctionAddress) {
Interceptor.attach(exportedFunctionAddress, {
onEnter: function(args) {
console.log("JNI getkey called");
},
onLeave: function(returnValue) {
try {
let keyResult = Memory.readUtf8String(returnValue);
console.log("Reconstructed key = " + keyResult);
returnValue.replace(ptr(keyResult));
} catch (memoryReadError) {
console.log("Memory read error: " + memoryReadError.message);
}
}
});
let retrievedKey = jni.getkey();
console.log("key =" + retrievedKey);
} else {
console.log("Failed to find the export 'Java_com_example_re11113_jni_getkey'");
}
}
function executeMain() {
Java.perform(function () {
interceptJNI();
});
}
setTimeout(executeMain);
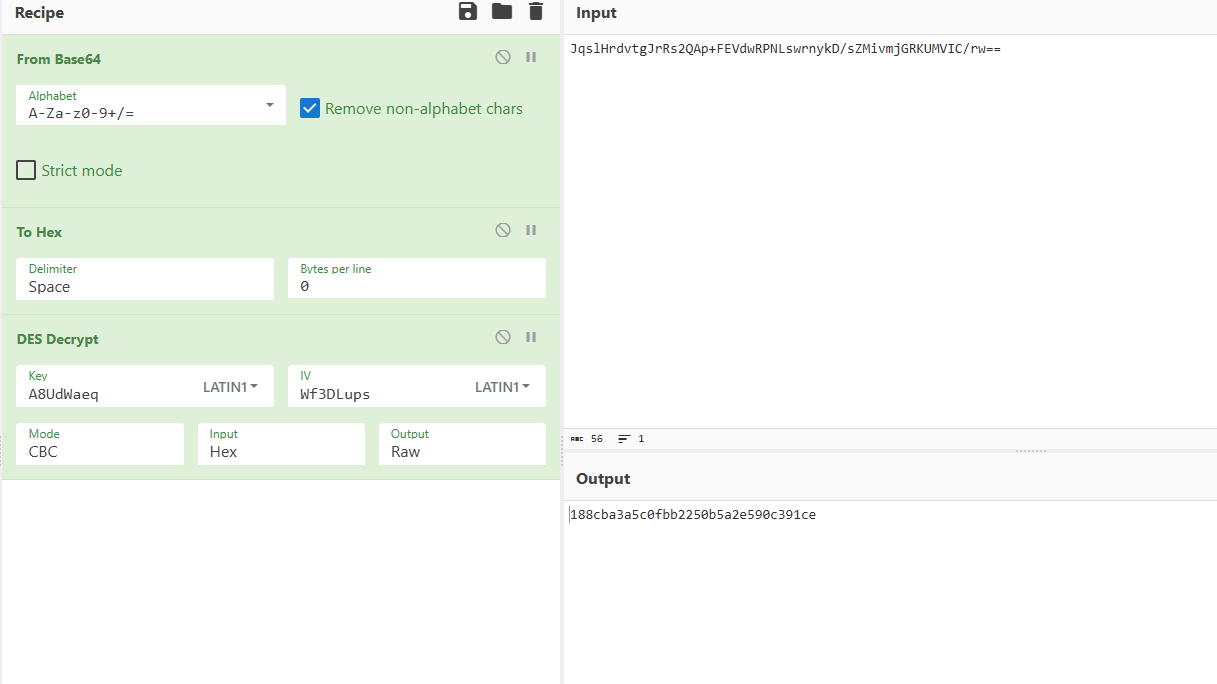
gdb_debug
多次异或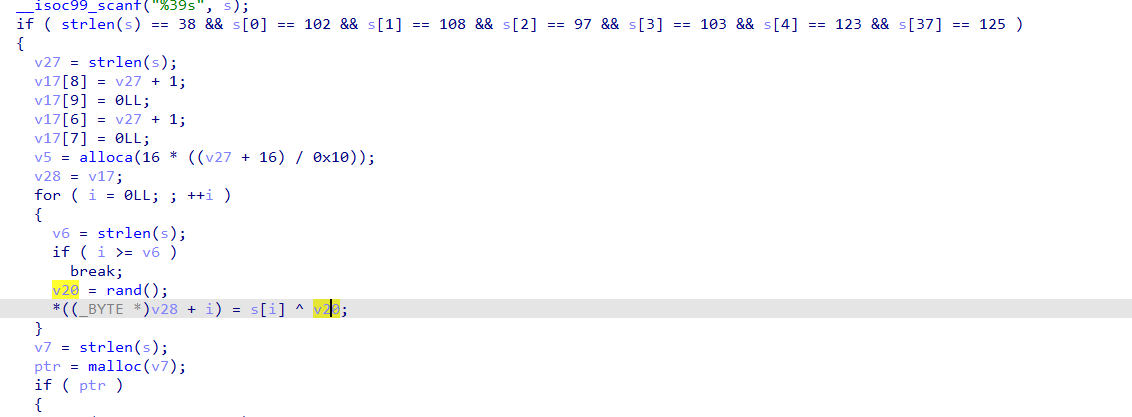
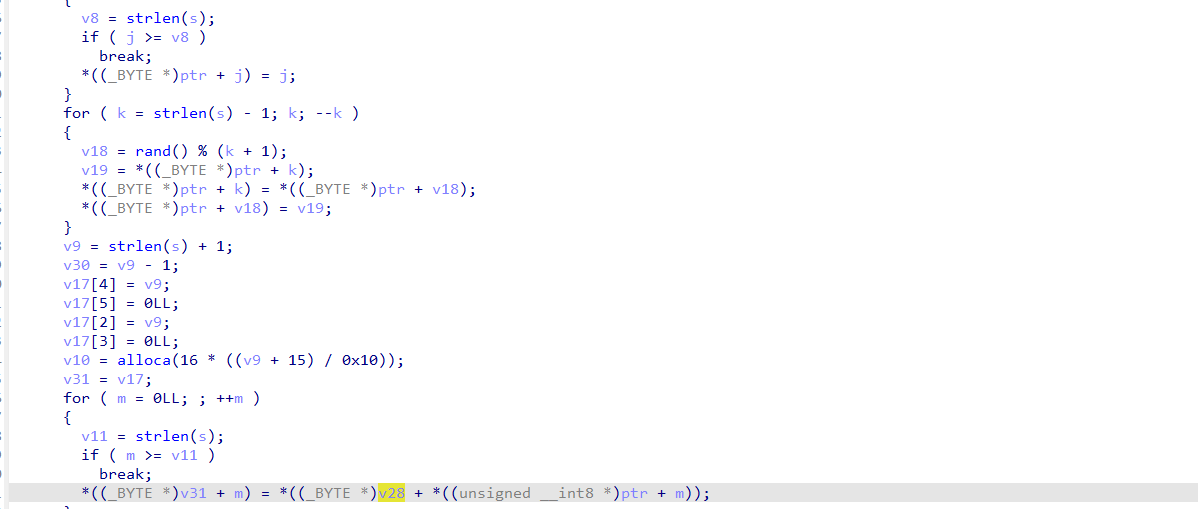
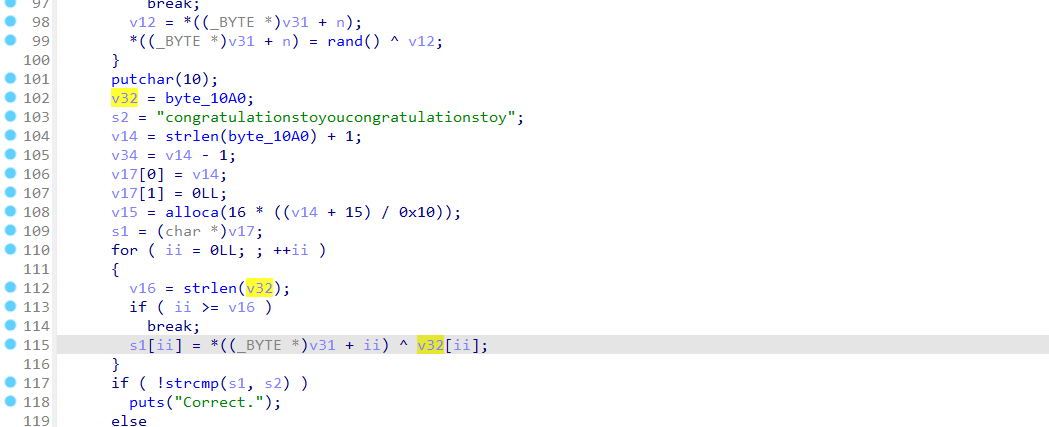
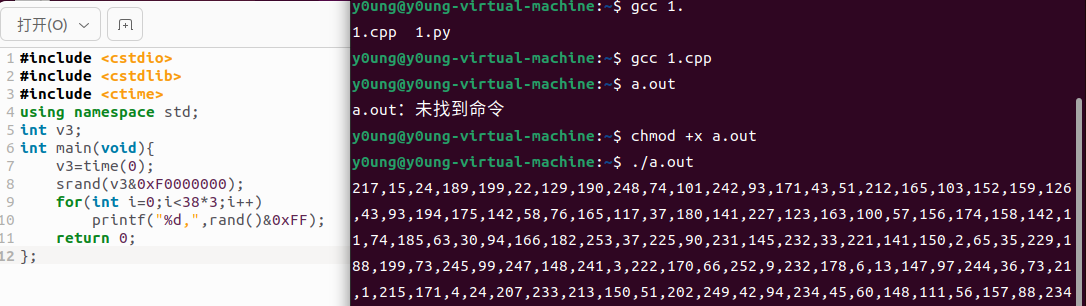
encstr="congratulationstoyoucongratulationstoy"
enc=[ord(ch)for ch in encstr]
rnd1=[0xBF, 0xD7, 0x2E, 0xDA, 0xEE, 0xA8, 0x1A, 0x10, 0x83, 0x73, 0xAC, 0xF1, 0x06, 0xBE, 0xAD, 0x88, 0x04, 0xD7, 0x12, 0xFE, 0xB5, 0xE2, 0x61, 0xB7, 0x3D, 0x07, 0x4A, 0xE8, 0x96, 0xA2, 0x9D, 0x4D, 0xBC, 0x81, 0x8C, 0xE9, 0x88, 0x78]
rnd2=[217,15,24,189,199,22,129,190,248,74,101,242,93,171,43,51,212,165,103,152,159,126,43,93,194,175,142,58,76,165,117,37,180,141,227,123,163,100]
rnd3=[0,1,0,0,4,5,1,1,4,0,6,3,3,8,10,13,4,15,2,13,10,12,3,21,24,20,11,26,24,9,29,10,31,32,0,10,0,33]
rnd4=[222,170,66,252,9,232,178,6,13,147,97,244,36,73,21,1,215,171,4,24,207,233,213,150,51,202,249,42,94,234,45,60,148,111,56,157,88,234]
perm=[0]*38
ret=[0]*38
for i in range(38):
enc[i]^=rnd1[i]
enc[i]^=rnd4[i]
perm[i]=i
for i in range(37,0,-1):
perm[i],perm[rnd3[i]]=perm[rnd3[i]],perm[i]
for i in range(38):
ret[perm[i]]=enc[i]
for i in range(38):
ret[i]^=rnd2[i]
print(chr(ret[i]&0x7F),end='')
whereThel1b
ida直接看很麻烦,fuzz一下
1-3位输出4位,4-6位输出8位,后面不影响前面的长度固定尝试爆破
import whereThel1b
encry = [108, 117, 72, 80, 64, 49, 99, 19, 69, 115, 94, 93, 94, 115, 71, 95, 84, 89, 56, 101, 70, 2, 84, 75, 127, 68, 103, 85, 105, 113, 80, 103, 95, 67, 81, 7, 113, 70, 47, 73, 92, 124, 93, 120, 104, 108, 106, 17, 80, 102, 101, 75, 93, 68, 121, 26]
alphabet = "abcdefghijklmnopqrstuvwxyzABCDEFGHIJKLMNOPQRSTUVWXYZ0123456789@#+/\{\}_-"
finalflag='a'*42
for r in range(14):
chk=0
for i in alphabet:
for j in alphabet:
for k in alphabet:
finalflag1=finalflag[:r*3]+i+j+k+finalflag[(r+1)*3:]
print(finalflag1)
finalflagbytes=finalflag1.encode()
whereThel1b.whereistheflag(finalflagbytes)
enced=whereThel1b.trytry(finalflagbytes)
if enced[r*4]==encry[r*4] and enced[r*4+1]==encry[r*4+1] and enced[r*4+2]==encry[r*4+2] and enced[r*4+3]==encry[r*4+3]:
chk=1
finalflag=finalflag1
break
if chk:
break
if chk:
break
print(finalflag)
CRYPTO
古典加密

转载请注明来源,欢迎对文章中的引用来源进行考证,欢迎指出任何有错误或不够清晰的表达.