REVERSE
baby_rop
调试过程中发现会在debug003和.text来回跳,应该就是题目说的ROP了
跟踪分析debug003段里的逻辑
长度校验

print(0x25649da8^0x25649d88)
#32
xor+add
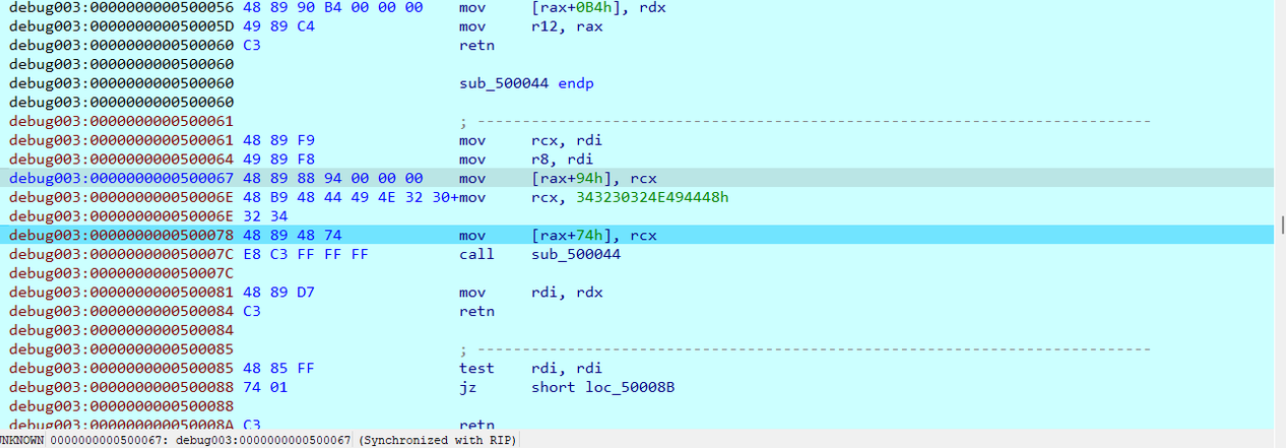
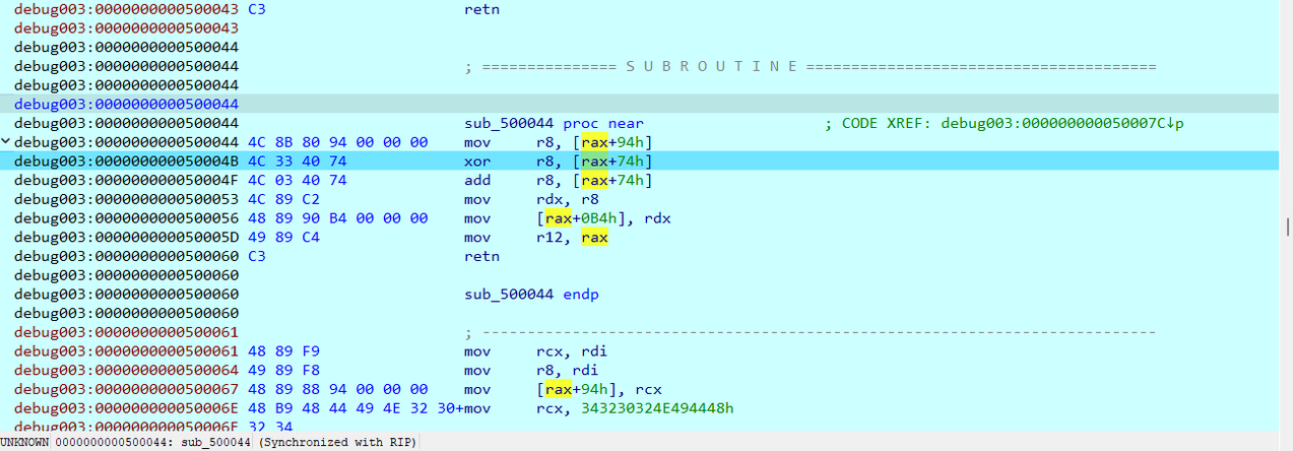

用idapython提取数据
from idaapi import get_reg_val
print('rax = '+hex(get_reg_val('rax')))
print('rsi = '+hex(get_reg_val('rsi')))
exp
rsi = [0x9a7ba6984ab8636b, 0x8f739f7345dc15cf,0x399f7938c150ea1a,0x7d454145674f5dd5]
tmp = [0x11db2a3f, 0x30836d0f,0xad48145,0x1ecb02bb]
for i in range(len(rsi)):
rsi[i] ^= tmp[i]
value = (rsi[i] - 0x343230324E494448) ^ 0x343230324E494448
print(bytes.fromhex(hex(value)[2:]).decode()[::-1],end="")
FinalEncrypt
简要分析,根据时间戳生成key,然后进行加密
>>> os.path.getmtime('./Encryption.exe.enc')
1715156422.0
>>> os.path.getmtime('./flag.md.enc')
1715156519.0
>>> hex(1715156422)
'0x663b35c6'
>>> hex(1715156519)
'0x663b3627'
动调改值得到key
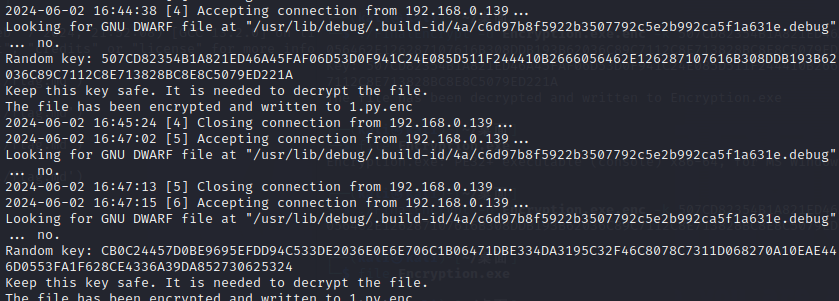
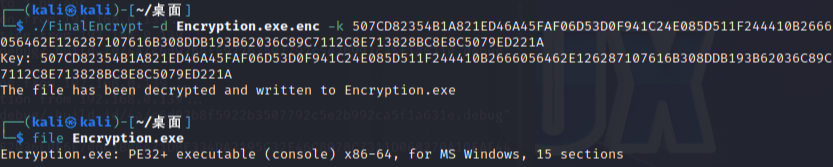
第二个程序还是根据时间戳生成,查表加密,用Encryption.exe的时间戳往后尝试
1715156464时,exp可以跑出来,时间戳相差不到一分钟
table = [
0x98, 0x87, 0x8C, 0x80, 0x09, 0x90, 0x94, 0x3E, 0xCB, 0xFA,
0x9C, 0xD0, 0x05, 0x2C, 0x50, 0x8D, 0x31, 0x79, 0x32, 0x86,
0x01, 0xA2, 0xBC, 0x0B, 0x56, 0x2F, 0x59, 0x54, 0x67, 0x5F,
0x89, 0x3B, 0x4C, 0x06, 0x68, 0xDD, 0xCD, 0xC4, 0x0C, 0x37,
0xCF, 0x5E, 0x1E, 0x0A, 0x8A, 0x23, 0xCA, 0xEE, 0xFF, 0x3C,
0xD8, 0x38, 0xE3, 0x6D, 0xFE, 0x61, 0xFC, 0xE9, 0x7B, 0x19,
0x10, 0xDC, 0x49, 0x8E, 0xF2, 0x78, 0xD7, 0xE1, 0xE0, 0x95,
0xA1, 0x5B, 0xA9, 0xC0, 0x2D, 0x48, 0xD2, 0x18, 0xD4, 0x7F,
0xA8, 0x2A, 0xFB, 0x16, 0xDB, 0x07, 0x4A, 0xA0, 0x91, 0x30,
0x45, 0xC2, 0xB1, 0xB7, 0xA3, 0x34, 0x2B, 0x14, 0x51, 0x00,
0xB8, 0xB6, 0xC8, 0x7E, 0xBE, 0x02, 0xF9, 0x84, 0xAB, 0xC7,
0x64, 0x53, 0xAA, 0x58, 0xBB, 0x74, 0x69, 0x66, 0xC3, 0x0E,
0x47, 0x4D, 0x21, 0xDA, 0xEB, 0x04, 0x08, 0x29, 0x00, 0x00,]
msg = [0xe0,0x78,0x16,0xe1,0xdb,0xa1,0xda,0x61,0x53,0x66,0x34,0xbe,0xf2,0xc3,0xb6,0x34,0x6d,0x53,0x3c,0xc3,0xb6,0xb8,0x34,0xe3,0xbe,0xb6,0x34,0xc8,0x02,0x64,0x14,0x3c,0x34,0xe3,0x64,0x00,0xbb,0x4d,0xaa,0x69,0x02,0xff,0x64,0x34,0x14,0xe3,0xb8,0x34,0x4d,0xff,0x66,0x34,0xb8,0xb6,0x6d,0xb6,0xbb,0xc3,0x38,0x34,0x14,0x34,0x61,0xab,0x14,0x7e,0x04]
for i in range(len(msg)):
print(chr(table.index(msg[i])),end='')
#DASCTF{7ou_h@ve_5o1ved_4he_fina1_4ncrypti0n_a4d_y0u_de5erv3_a_7lag}
MISC
Ez_mc
翻存档

PASS=HDCTFWIN!
https://www.bilibili.com/read/cv15050852/

https://sdercolin.github.io/utaformatix3/
转换一下
最后面疑似01
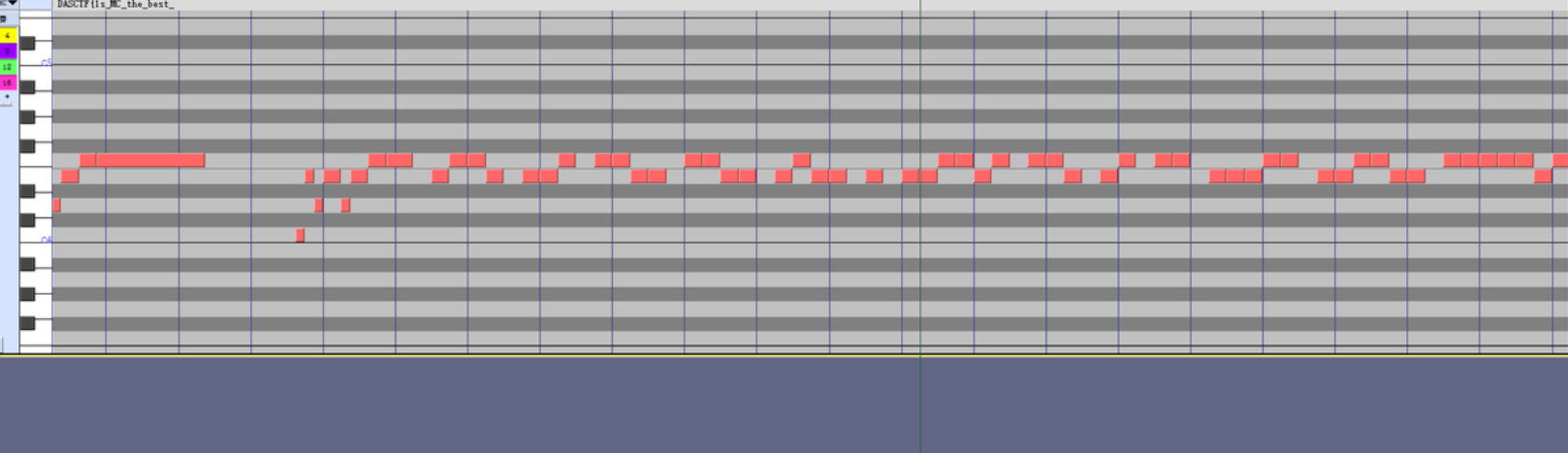
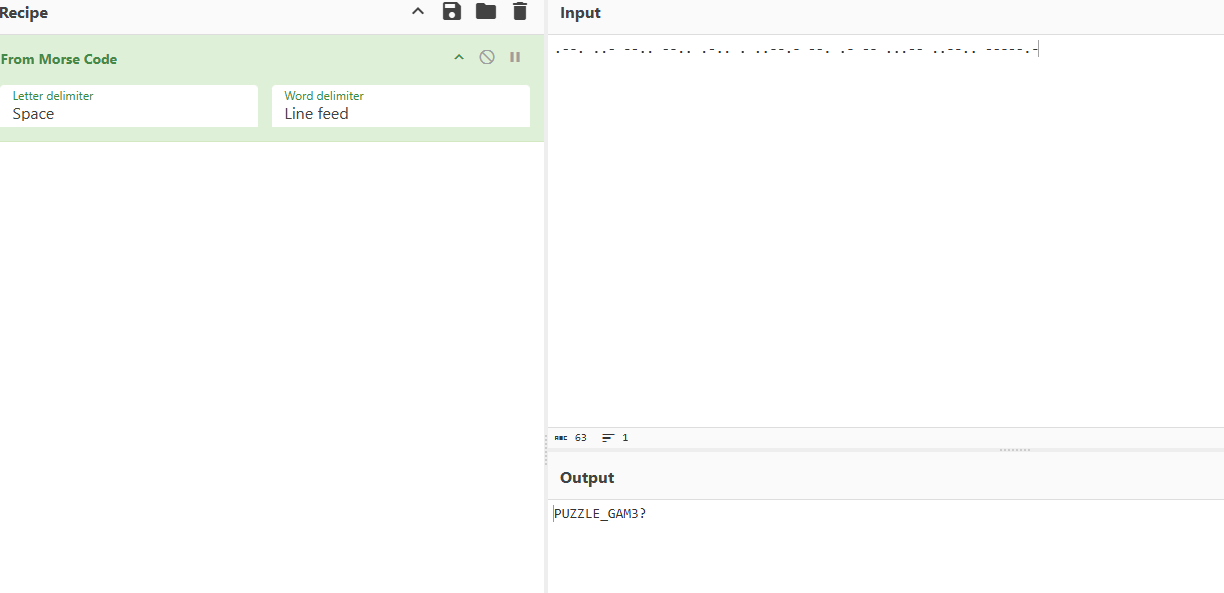
DASCTF{1s_MC_the_best_PUZZLE_GAM3?}
转载请注明来源,欢迎对文章中的引用来源进行考证,欢迎指出任何有错误或不够清晰的表达.